Viruses themselves as a computer threatnobody is surprised today. But if earlier they affected the system as a whole, causing failures in its performance, today, with the advent of such a species as a crypto virus, the actions of a penetrating threat concern more user data. It is perhaps even more of a threat than Windows destructive executable applications or spyware applets.
What is a virus cipher?
The code itself is written in self-copying.virus, involves the encryption of almost all user data special cryptographic algorithms that do not affect the system files of the operating system.

At first, the logic of the impact of the virus was not muchquite understandable. Everything became clear only when the hackers who created such applets began demanding money to restore the initial file structure. At the same time, the penetrating virus-cipher virus himself cannot decrypt files due to their peculiarities. To do this, you need a special decoder, if you want, a code, password, or algorithm required to restore the desired content.
The principle of penetration and operation of the virus code
Как правило, «подцепить» такую гадость в The internet is hard enough. The main source of spreading "contagion" is e-mail at the level of programs installed on a specific computer terminal like Outlook, Thunderbird, The Bat, etc. We note right away: Internet mail servers do not concern this, since they have a sufficiently high degree of protection and access user data is possible except at the cloud storage level.
Another thing - the application on the computerthe terminal. It is here that the field for viruses is so wide that it is impossible to imagine. True, here, too, it is worth making a reservation: in most cases, large companies aim at viruses, from which you can “tear off” money for providing a decryption code. This is understandable, not only completely confidential information can be stored on the servers of such companies, but also on the servers of such companies, but also files, so to speak, in a single copy that cannot be destroyed in any way. And then the decryption of files after the encryption virus becomes quite problematic.
Of course, an ordinary user canundergo such an attack, but in most cases this is unlikely if you follow the simplest recommendations for opening attachments with extensions of an unknown type. Even if the email client detects an attachment with the extension .jpg as a standard graphic file, you must first check it with a regular anti-virus scanner installed in the system.

If you do not, when you open the doubleby clicking (standard method), activation of the code will start, and the encryption process will start, after which the same Breaking_Bad (encryption virus) will not only be impossible to delete, but the files will not be restored after the threat has been removed.
The general effects of penetration of all viruses of this type.
As already mentioned, most viruses of thisType of penetrate the system through e-mail. Well, let's say, a large organization, a specific registered mail, receives a letter with content like “We changed the contract, scan in the attachment” or “A delivery note was sent to you for the shipment of the goods (a copy there)”. Naturally, the unsuspecting employee opens the file and ...
All office-level user filesdocuments, multimedia, specialized AutoCAD projects, or any other archival data are instantly encrypted, and if the computer terminal is in a local network, the virus can be transmitted further by encrypting data on other machines (this becomes noticeable immediately after system braking and programs or currently running applications).

At the end of the encryption process, the virus itself,apparently, it sends a kind of report, after which the company may receive a message that such and such a threat has entered the system, and that only such and such an organization can decipher it. This usually concerns the [email protected] virus. Next comes the requirement to pay for decryption services with the proposal to send several files to the client's email, which is most often fictitious.
Code Harm
If anyone has not understood:Decrypting files after the encryption virus is a rather laborious process. Even if you are not “led” to the demands of intruders and try to use the official state structures to combat computer crimes and prevent them, usually nothing good happens.
If you delete all files, restoresystem and even copy the original data from removable media (of course, if there is such a copy), all the same, if the virus is activated, everything will be encrypted again. So you shouldn’t be too flustered, especially since when inserting the same flash drive into a USB port, the user will not even notice how the virus encrypts the data on it. That's when you can’t get problems.
Firstborn in the family
Now pay attention to the firstencryption virus. Nobody has yet thought how to cure and decrypt files after exposure to executable code enclosed in an email attachment with a dating proposal. The realization of the scale of the disaster came only with time.
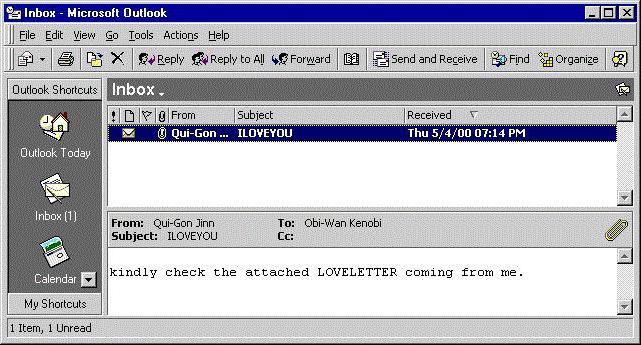
That virus had the romantic name "I LoveYou. " The unsuspecting user opened the attachment in the electronic message and received completely non-reproducible multimedia files (graphics, video and audio). Then, however, such actions looked more destructive (harming the user media libraries), and nobody demanded money for it.
Newest Mods
As you can see, the evolution of technology has become enoughprofitable business, especially considering that many leaders of large organizations instantly run to pay for the decryption actions, without thinking at all that you can lose both money and information.
By the way, do not look at all these "left"posts on the Internet, they say, "I paid / paid the required amount, they sent me a code, everything was restored." Nonsense! All this is written by the developers of the virus themselves in order to attract potential, sorry, "suckers." But, by the standards of an ordinary user, the amounts for payment are quite serious: from a hundred to several thousand or tens of thousands of euros or dollars.
Теперь посмотрим на новейшие типы вирусов такого types that were fixed relatively recently. All of them are practically similar and belong not only to the category of encrypters, but also to the group of so-called extortionists. In some cases, they act more correctly (like paycrypt), like sending out official business proposals or reports that someone cares about the security of the user or organization. Such a virus encrypter simply misleads the user with his message. If he takes even the slightest action to pay, all - "divorce" will be complete.
XTBL virus
The relatively recent virus XTBL canattributed to the classic version of the cryptographer. As a rule, it penetrates the system through e-mail messages that contain attachments in the form of files with the .scr extension, which is standard for the Windows screensaver. The system and the user think that everything is in order, and activate the viewing or saving attachments.
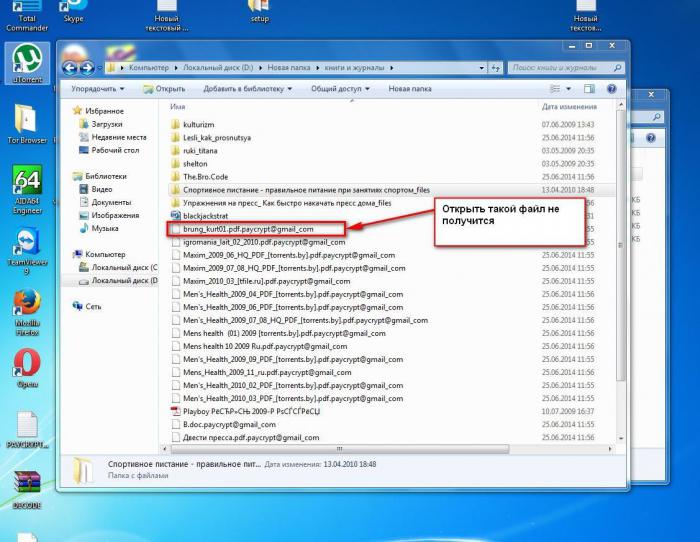
Alas, this leads to sad consequences:file names are converted to a set of characters, and the .xtbl is added to the main extension, after which a message is received at the required mail address about the possibility of decryption after payment of the specified amount (usually 5,000 rubles).
CBF virus
This type of virus also belongs to the classics of the genre.It appears in the system after opening e-mail attachments, and then renames user files, adding at the end an extension like .nochance or .perfect.
Unfortunately, decryption cipher virusThis type of analysis of the contents of the code, even at the stage of its appearance in the system, is not possible, since after the completion of its actions, it performs self-destruction. Even such, as many believe, a universal remedy, like the RectorDecryptor, does not help. Again, the user receives a letter demanding payment, which is given for two days.
Breaking_Bad virus
This type of threat works in the same way, but renames files in the standard version, adding to the .breaking_bad extension.
This situation is not limited.Unlike previous viruses, this one can create another extension - .Heisenberg, so it is not always possible to find all infected files. So Breaking_Bad (encryption virus) is quite a serious threat. By the way, there are cases when even the licensed package of Kaspersky Endpoint Security 10 misses this type of threat.
[email protected] virus
Here is another, perhaps the most serious threatwhich is directed mostly to large commercial organizations. As a rule, a letter arriving in some department seems to contain a change to the supply agreement, or even just an invoice. An attachment may contain a regular .jpg file (such as an image), but more often, an executable .js script (Java applet).

How to decrypt the encryption virus of this type?Judging by the fact that there is used some unknown algorithm RSA-1024, no way. If we start from the name, we can assume that this is a 1024-bit encryption system. But, if anyone remembers, today 256-bit AES is considered the most perfect.
Encryption virus: how to disinfect and decrypt files with antivirus software
To date, to decipher the threats of suchNo solution type has yet been found. Even such masters in the field of anti-virus protection as Kaspersky, Dr. Web and Eset, can not find the key to solving the problem when the encryption virus has inherited from the system. How to cure files? In most cases, it is proposed to send a request to the official site of the antivirus developer (by the way, only if the licensed software of this developer is in the system).
In this case, you need to attach several encryptedfiles as well as their “healthy” originals, if any. In general, by and large very few people keep copies of data, so the problem of their absence only aggravates an already unfavorable situation.
Possible ways to identify and eliminate the threat manually
Yes, scanning with conventional antivirus threats identifies and even removes them from the system. But what to do with the information?
Some try to useprograms-decoders like the already mentioned utility RectorDecryptor (RakhniDecryptor). We note immediately: this does not help. And in the case of the Breaking_Bad virus, it can only do harm. And that's why.
Дело в том, что люди, создающие такие вирусы, trying to protect themselves and to instruct others. When using utilities for decryption, the virus can react in such a way that the whole system will “fly off”, and with complete destruction of all data stored on hard disks or in logical partitions. This, so to speak, is an indicative lesson for the edification of all those who do not want to pay. It is necessary to hope only on official anti-virus laboratories.
Cardinal methods
However, if things are really bad, you have todonate information. To completely get rid of the threat, you need to format the entire hard drive, including virtual partitions, and then install the "OS" again.

Unfortunately, there is no other way out. Even a system rollback to a specific saved restore point will not help. The virus may disappear, but the files will remain encrypted.
Instead of an afterword
In conclusion, it is worth noting that the situation is as follows:the virus encryptor penetrates the system, does its dirty work and is not treated by any known means. Antivirus protection was not ready for this type of threat. It goes without saying that you can detect or remove the virus after exposure. But the encrypted information will remain in unsightly form. So I would like to hope that the best minds of antivirus software development companies will still find a solution, although, judging by the encryption algorithms, it will be very difficult to do. Recall at least the Enigma encryption machine, which during the Second World War was in the German fleet. The best cryptographers could not solve the problem of the algorithm for decrypting messages until they got hold of the device. So it is here.