In this article we will discuss the concept of DMZ in detail.We will try to answer the questions about what a DMZ is, how it appeared, and how to set up the DMZ. Everyone will be able to gather at least general information on this topic.

The causes of the demilitarized zones
Now it's less and less common to see any companies without computers. And where there are computers, there is an internal local network that unites them.
In itself, the presence of a common internal localnetwork - it is very practical and safe. But with the advent of the worldwide Internet, everything has become a bit more complicated. Now the absolute majority of companies use the services of the World Wide Web. This greatly facilitates the workflow, as everyone can find in any seconds, any information of interest to him.
But with the development of the Internet there was also a threatpenetration into the company's general network from outside. First of all, it concerned companies that have public Internet services, available to any user of the World Wide Web. The danger was that the attacker, having access to the web service, could also gain access to personal information stored on any of the computers connected to the internal local network. This caused a number of difficulties, which are solved by creating a DMZ.
Original Source
The first thing you should know about DMZ, what is it, firstturn, military term, originating from the designation "demilitarized zone". It means a certain area of territory located between two opposing states. It prohibits any form of military activity - be it a special operation, diversion or espionage.
DMZ demilitarized zone: architecture and implementation
From the interpretation of the original term to usit becomes clear that the DMZ is a specific section of the terrain on which any kind of harmful activity is prohibited. And this is extremely successful characterizes the whole essence of this, let's say, tricks.
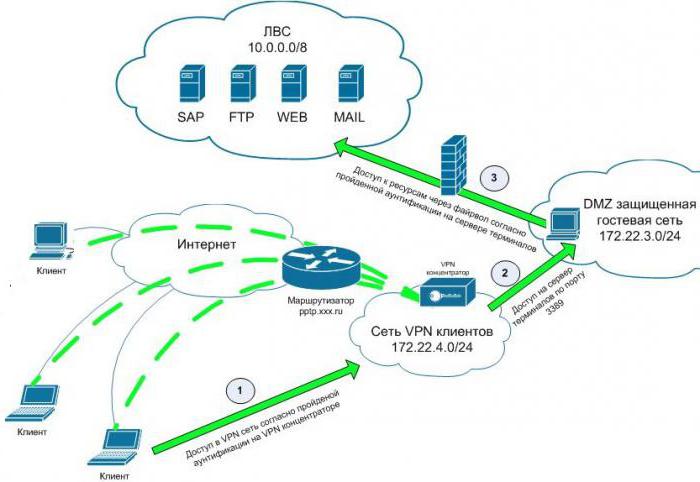
We need to understand the very concept of DMZ, thatthis is an extremely simple solution, which is the creation of a separate segment of a computer network that is isolated from all external Internet hosting and from the internal network of the company. Also this restriction of control or a complete ban on access to both the Internet and the internal network.
Create a separate network segment is easy enough.For this, firewalls or firewalls are used. The very word "firewall" to an ordinary user can be known from films about known hackers, but very few people know what he is.
A firewall is a software / hardwarea unit of a computer network that divides it into sectors and allows filtering incoming network traffic according to the rules specified by the operator (administrator). Also, in case of unauthorized access, the attacker only gets access to those files that are located within the separated sector, without prejudice to the others.
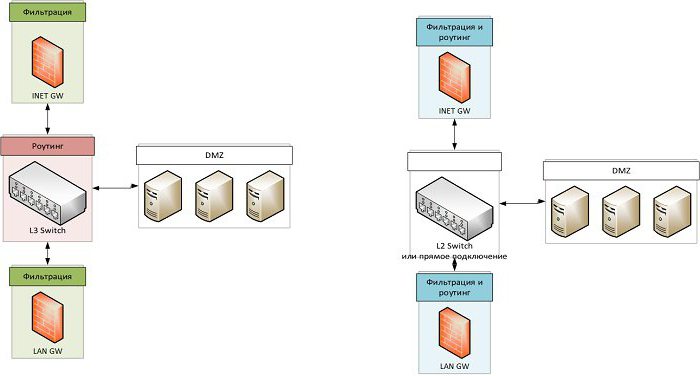
There are at least two types of configuration of the demilitarized zones - with one firewall or with multiple. In the first configuration, the firewall divides the network into three sectors:
- internal network;
- DMZ;
- Internet channel.
But still this method provides insufficientlevel of protection. Most large firms still use the second method - with a large number of firewalls. In this case, the attacker will have to overcome at least one additional system perimeter with its own traffic filter, which greatly increases security.
Customize
Sure, many are already sufficientlyasked about the DMZ, that it is an easy and effective way to ensure the security of your computer network. Users of multichannel Internet routers can appreciate this ingenious trick for hackers themselves.
Всё, что требуется для настройки DMZ, это вывести one device as a local network, connecting it, respectively, through a separate cord to the free socket of the router, then assign it a static IP address, then activate it in the DMZ window and restart the device.
Before all manipulations you should make sure thatall devices have the latest versions of protection. After that, you can freely use this, albeit simple, but effective protection against encroachment on your personal data.
This article briefly outlined the most important facts about the DMZ: what it is, how it works, and, most importantly, its purpose.











