Undoubtedly, many computer users,working with the Internet (and not only), heard about the term, like encryption of AES data. What kind of system it is, what algorithms it uses and for what it is used, has a fairly limited circle of people. Usual user is by and large to know and do not need. Nevertheless, we will consider this cryptographic system, especially without going into complex mathematical calculations and formulas, so that it is understandable to any person.
What is AES encryption?
To begin with, the system itselfrepresents a set of algorithms that make it possible to hide the initial form of some data that is transmitted, received by the user or stored on the computer. Most often it is used in Internet technologies, when it is required to ensure complete confidentiality of information, and refers to the so-called symmetric encryption algorithms.

Тип шифрования AES предполагает использование для convert information into a protected view and reverse decode the same key that is known to both the sending and receiving parties, in contrast to symmetric encryption, which involves the use of two keys - closed and open. Thus, it is easy to conclude that if both sides know the right key, the process of encryption and decryption is quite simple.
A bit of history
For the first time, AES encryption was mentioned back in 2000, when the Rijndael algorithm became the winner in the selection contest for the DES successor, which was the standard in the US since 1977.
In 2001, the AES system was officially adopted as the new federal standard for data encryption and has since been used universally.
Types of AES encryption
The evolution of algorithms included severalintermediate stages, which were mainly associated with increasing the length of the key. Today, there are three main types: AES-128-encryption, AES-192 and AES-256.

The name speaks for itself.The numerical designation corresponds to the length of the key used, expressed in bits. In addition, AES encryption refers to a block type that works directly with blocks of information of fixed length, encrypting each of them, unlike streaming algorithms that operate with single symbols of an open message, translating them into an encrypted form. In AES, the block length is 128 bits.
In scientific terms, the same algorithms,which use AES-256-encryption, mean operations based on the polynomial representation of operations and codes when processing two-dimensional arrays (matrices).
How it works?
The algorithm is rather complicated, howeverincludes the use of several basic elements. Initially, a two-dimensional matrix, conversion cycles (rounds), a round key and tables of initial and reverse substitutions are used.
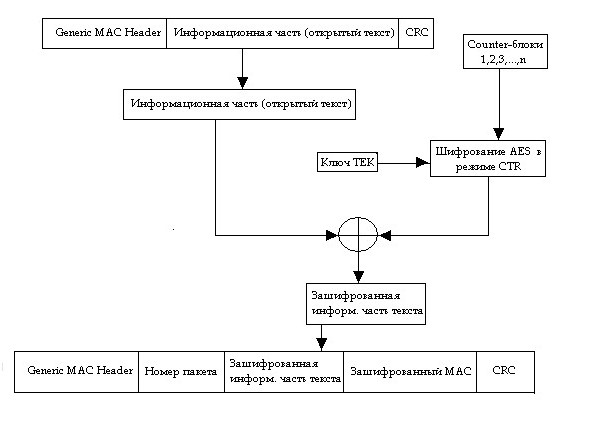
The process of data encryption consists of several stages:
- Calculation of all round keys;
- substitution of bytes using the main S-Box table;
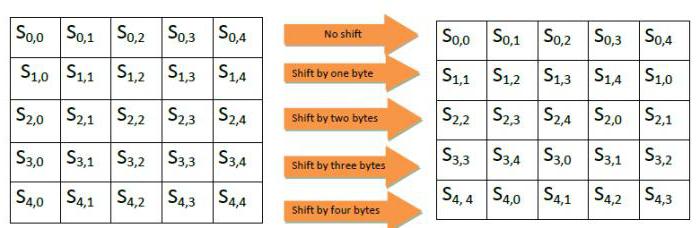
- shift in the form using different values (see the figure above);
- the mixing of data within each column of the matrix (form);
- Add a shape and a round key.
The decryption is done in the reverse order, but instead of the S-Box table, the reverse setting table is applied, which was mentioned above.

If you give an example, if you have a key length of 4bit, it takes only 16 stages (rounds), that is, you need to check all possible combinations, starting with 0000 and ending with 1111. Naturally, such protection is hacked quickly enough. But if we take more keys, for 65 bits, 65 536 steps are required, and for 256 bits - 1.1 x 1077. And as it was stated by American specialists, the selection of the right combination (key) will take about 149 trillion years.
What to apply when setting up the network in practice: AES or TKIP encryption?
Now we turn to the use of AES-256 when encrypting transmitted and received data in wireless networks.

As a rule, in any router (router)there are several options to choose from: only AES, only TKIP and AES + TKIP. They are used depending on the protocol (WEP or WEP2). But! TKIP is an obsolete system because it has less protection and does not support 802.11n connections with a data transfer rate exceeding 54 Mbps. Thus, the conclusion about the priority use of AES together with the security mode WPA2-PSK suggests itself, although it is possible to use both algorithms in a pair.
The reliability and safety of AES algorithms
Despite the loud statements of specialists,the algorithms of AES are theoretically still vulnerable, since the very nature of encryption has a simple algebraic description. This was noted by Niels Fergusson. And in 2002, Josef Pepshik and Nicolas Courtois published an article that justifies the potentially possible attack of XSL. True, it has caused a lot of controversy in the scientific world, and some have considered their calculations to be erroneous.
In 2005, it was suggested thatThe attack can use third-party channels, not just mathematical calculations. In this case, one of the attacks computed the key after 800 operations, and the other received it after 232 operations (in the eighth round).
Without a doubt, for today thissystem and could be considered one of the most advanced, if not one but. A few years ago, on the Internet, a wave of virus attacks took place, in which the virus-encryptor (and at the same time also the extortionist) penetrating the computers, completely encrypted the data, demanding a tidy amount of money for deciphering. In this message, it was noted that the encryption was performed using the algorithm AES1024, which, as was thought until recently, does not exist in nature.
So it or not, but even the most famousthe developers of anti-virus software, including Kaspersky Lab, were powerless to decrypt the data. Many experts recognized that the notorious I Love You virus, which at one time hit millions of computers around the world and destroyed important information on them, compared to this threat, turned out to be a childish babble. In addition, I Love You was more focused on multimedia files, and the new virus only accessed the confidential information of large corporations. However, to state with all evidence that the encryption of AES-1024 was used here, no one takes it.
Conclusion
If you sum up some result, in any case, you canTo say that AES encryption is by far the most advanced and secure, no matter which key length is used. It is not surprising that this standard is used in most cryptosystems and has quite broad prospects for development and improvement in the foreseeable future, especially since it is very likely that several types of encryption can be combined into one (for example, the parallel use of symmetric and asymmetric or block and streaming encryption).










