Not so long ago, the organization of local networksrequired mandatory use of the correct protocol. This choice influenced what types of computers can be connected to it. Today, such a problem has practically disappeared. Modern TCP network protocols have replaced everything that existed before. This is a universal solution that can be used in any operating system.

Terminology
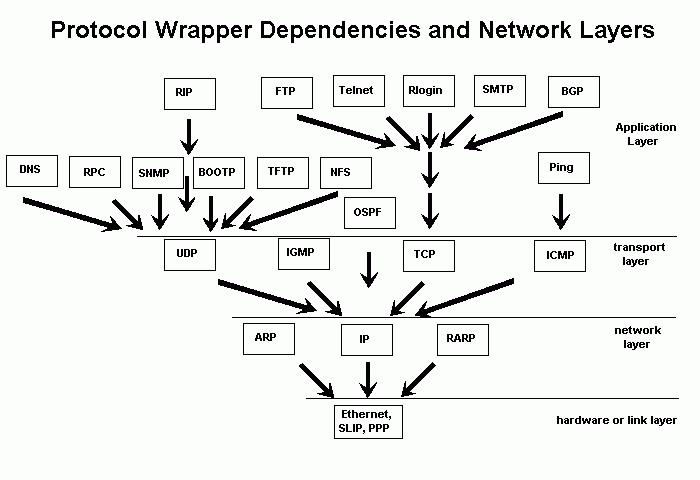
A network protocol is an installed language,which is the communication programs. Data transfer is the movement of some bitstream over the cable. In order for it to reach the target computer and appear in it as data, a certain set of rules is required. They are also registered in standard protocols. They are usually told about them that they have a level of nesting. What does it mean? There is a physical layer, which is a list of definitions, for example, how can a network cable, the thickness of its veins and other parameters. Let's say we are talking about a working cable. Then the data packets will be sent along it. But which computer will take them? Here the channel level is turned on, and the header of the packets indicates the physical address of each machine-a certain number sewn into the network card. It is called the MAC address.

Network hierarchy
The link layer is the same as Ethernet.The package contains a set of specific parameters that specify its type. Data is directly dependent on this type, and their content refers to the network layer. There are two most common protocols: ARP, which is responsible for converting IP addresses to MAC, and the IP protocol itself. You can bring the structure of the IP packet. All data that is transferred with it is already sent to a specific network address. In the package there is a number in the established format, indicating the type of protocol.
The most common are two types:TCP and UDP. Between them there is a certain difference, consisting in the fact that the first is characterized by the maximum degree of reliability, because when sending a packet, it constantly sends a request for its receipt. The second network protocol is a convenient tool, for example, when listening to Internet radio. In this case, it is supposed to send packets without any verification of the fact of their receipt. If he has reached, then you can listen to the radio, and if not - then there is no sense in checking and monitoring.

Package Delivery Features
The package necessarily indicates the port number, wheresending. Usually this parameter is determined by the type of protocol at the application level - depending on the application to which the information is directed. You can use non-standard service ports, no one forbids it. The most known network protocols in this case are HTTP and POP3. Gets a specific hierarchy of nested packages. The Ethernet packet contains IP, then TCP or UDP, and then data that is specific to the application.

Distinctive characteristics
Network protocol, unlike protocolsdata transfer, is not tied to certain equipment. Their implementation occurs at the software level, so they can be installed and deleted at any time.
IP and TCP / IP
This network protocol is used not only innetwork Internet, but also within the operating system itself. It represents the transport and network layer, so that the data is transmitted by blocks. Very long years it was used only on UNIX-networks, and now, when the Internet has grown quite rapidly, the IP network protocol has been used in almost every kind of local computer networks. At the moment, it serves as the main protocol for most services running on operating systems.
Local and switched networks
Old network protocols required some sort ofspecific knowledge, and TCP / IP is used by such users who have never even seen network cards. Access to the Internet using a modem or a local network is provided provided the same protocol is used. And the process of setting it completely depends on the type of connection used in this case. It is worth noting that the network layer protocols differ from all others, and the parameters for accessing the local network or using a modem also have certain nuances. A dial-up connection is best installed using the automatic configuration program provided by the provider. Otherwise, you must manually enter all the necessary parameters. You can consider the basic network protocols.

IPX Protocol
This kit was developed by Novell withthe purpose of using NetWare for its own OS. IPX is partly similar to TCP / IP, that is, it includes some of the protocols in this package, but the company has protected it with copyright. However, Microsoft Corporation has created its own protocol, compatible with this, designed for operating systems from the Windows family. IPX is a network protocol, which in terms of functionality is similar to IP. SPX is a tool for the transport layer, which is designed to provide packet data exchange between individual machines.
At the moment, this protocol is used only innetworks with servers where old versions of the NetWare operating system are installed. It is often used with any other set of network protocols. Now Nowell has completely switched to the new universal TCP / IP protocol.
NetBEUI
This network protocol is used in networks of smallsizes. It was first introduced in Windows NT 3.1, as well as in several subsequent versions of this system, where it was used by default. In recent versions of systems, TCP / IP already known to us has taken its place. This protocol is quite simple, it lacks many of the functions used in more advanced versions. It is not suitable for internetwork data exchange. It can be useful for a simple peer-to-peer network, but now it is not even represented as a standard component of the OS, it needs to be installed independently from the disk.
NetBEUI is a convenient tool for creating a direct cable connection, and in this sense it is the minimum protocol that is required to form a peer-to-peer network in Windows 9x versions.
conclusions
It is important to remember certain points.At the moment there is no longer a single network protocol. All of them are intended for communication, but each of them has completely different tasks, there are advantages and disadvantages in comparison with the others. The use of each of them implies the existence of certain working conditions, which are usually prescribed by the protocol itself. When choosing a solution, it is worth relying on this parameter.







